1. What Is the Key Vault Parameters Form (and Why It Matters)?
Dynamics 365 F&O implementations often call external services—payment gateways, tax engines, storage accounts—and all of them need credentials or tokens. Hardcoding those values in X++ or config files is a security risk. Azure Key Vault is Microsoft’s secure secrets storage, and the Key Vault parameters form in D365 F&O is your bridge to fetch those secrets safely at runtime.
Benefits of using the Key Vault parameters form:
- Centralized secret management system.
- Least-privilege access via Azure AD (Microsoft Entra ID) and Key Vault access controls (Access Policies or RBAC).
- No credentials need to be hardcoded in X++, batch jobs, or data integrations.
2. Architecture Flow
- Azure Key Vault holds one or more secrets
- Azure AD App Registration provides client ID/secret
- D365 F&O stores the key vault URL and the client id and secret in the Key Vault parameters form.
- Runtime flow: D365 authenticates to Azure AD → requests the secret from azure key vault → returns it to your code/config using D365 classes.
3. Prerequisites Checklist
- Azure subscription with rights to create or manage Key Vault.
- Rights to register an application in Azure AD / Microsoft EntraID.
- D365 FO with systemadmin role to configure the Key Vault parameters form.
- Optional : A service account that will consume the secrets via batch job, X++ class.
4. Step-by-Step: Create the Azure Key Vault
- Go to Azure → Create a resource → Key Vault.
- Basics
- Subscription & Resource group: Choose a subscription and resource group.
- Name: Name should be unique.
- Region: align with your D365 region if possible.
- Pricing tier: Standard should be fine.
- Access configuration
- Access policy (classic): Add policies later.
- RBAC (recommended): Role-based access.
- Review + Create → Deploy. This will create the Key vault.
Add Secrets to the Vault
- Vault → Objects → Secrets → + Generate/Import.
- Secret name: It should be a clean and logical (e.g.,
ConnectionString,etc). - Secret value: Paste the actual key in the value field.
- Set expiration and reminders for rotation (This is optional and should be used for best security)
5. Step-by-Step: Register an App in Azure AD
- Azure Portal → Microsoft Entra ID → App registrations → New registration.
- Name:
D365-FNO-KeyVault-Reader-UAT(or similar). - Supported account types: “Accounts in this organizational directory only” (typical).
- Redirect URI: Not required for client secret flows; skip.
- Register → Copy the Application/Client ID and Tenant ID.
- Certificates & secrets → New client secret → Add description & expiry → Copy the secret value as it will vanish after you close the browser.
Tip: Securely store this client secret. D365 F&O mostly uses the client ID/secret pattern to call Azure key vault.
6. Grant the App Access to the Key Vault
Your App Registration needs Get and List permissions on secrets.
Option A: If you choose Access Policies (Classic)
- Vault → Access policies → + Create (or Add Access Policy).
- Secret permissions: Get, List.
- Principal: Select your App Registration.
- Save.
Option B: If you choose RBAC (Recommended)
- Vault → Access control (IAM) → Add role assignment.
- Role: Key Vault Secrets User (allows get/list).
- Assign to: Your App Registration.
- Save.
7. Configuring the Key Vault Parameters Form in D365 FO
Path: System administration → Setup → Key Vault parameters
Fields:
- Key Vault URL: This should be something like this →
https://<your-vault-name>.vault.azure.net/ - Client ID: Application/Client ID from the App Registration.
- Client Secret: In the secret grid, value we generated earlier(Attached screenshot for reference).
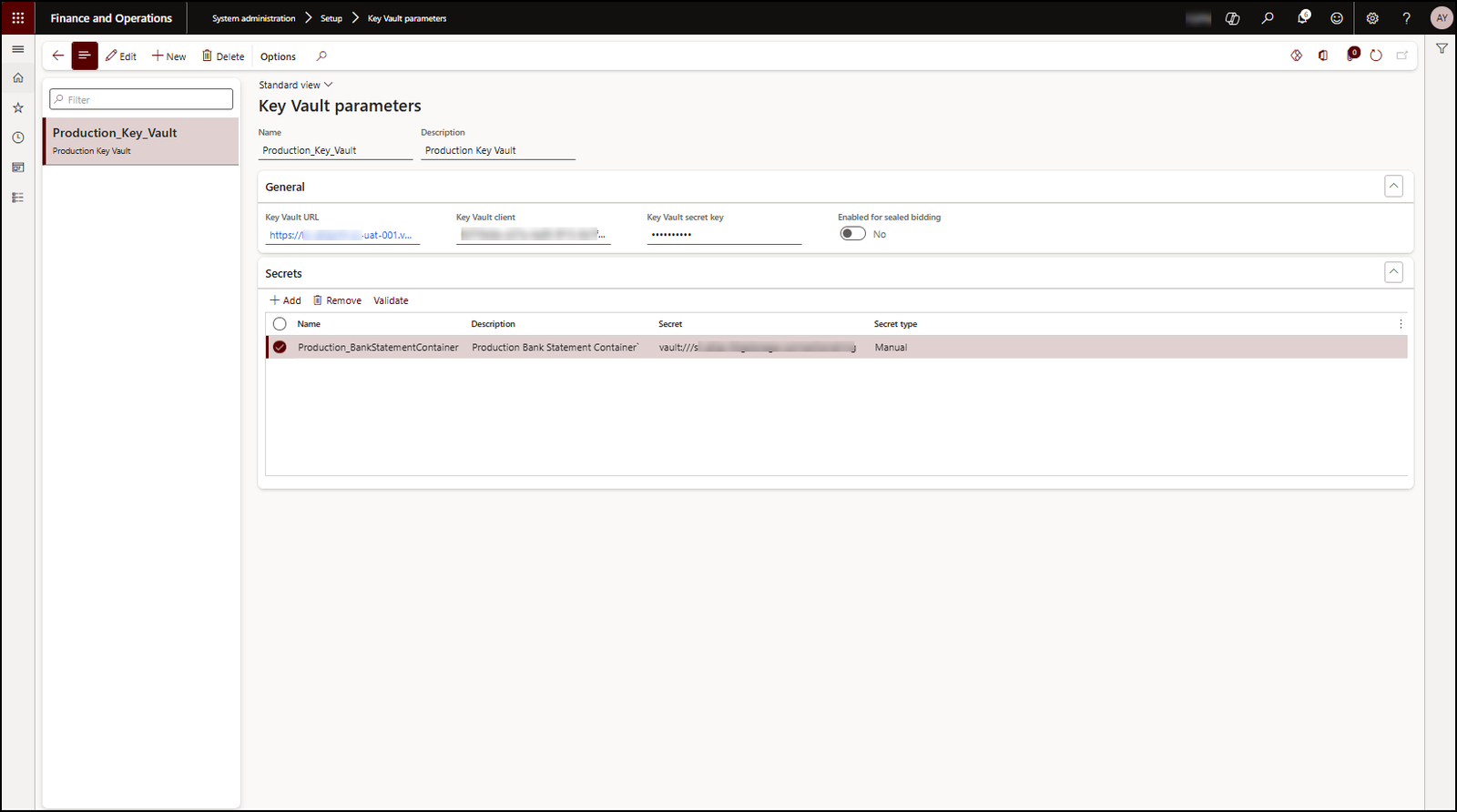
Security note: Access to this form should be restricted only to a small admin group should be able to view or edit it.
8. Consuming the Secret in X++ (Code Example)
Once the parameters are set, code anywhere in D365 can fetch secrets.
///
/// Fetch a secret from Azure Key Vault through D365’s KeyVaultConfiguration class
///
public static str getSecretValue(str _secretName)
{
KeyVaultCertificateTable KeyVaultCertificateTableLocal;
str secretValue;
secretValue = KeyVaultCertificateHelper::getManualSecretValue(KeyVaultCertificateTable::findByName('KeyVaultSecretKeyName').RecId)
return secretValue;
}
9. Final Words
The Key Vault parameters form is your one-time, secure setup to standardize secret retrieval in D365 F&O. After configuring it:
- Add secrets for every external service you use.
- Refactor existing scripts and classes to use
KeyVaultCertificateHelperinstead of hardcoded credentials.
Happy (and secure) integrating!
Need help? Connect Atul
- Key Vault parameters in Dynamics 365 F&O - July 29, 2025
- User-based authentication RSAT - July 22, 2025
- Boost First-Load Performance in Dynamics 365 F&O with IIS Preload - July 15, 2025