Seamless RSAT Sign-In After Certificate Retirement:
Microsoft is phasing out certificate-based authentication for Dynamics 365 F&O apps. Because the Regression Suite Automation Tool (RSAT) can’t authenticate with service principals, user-based sign-in is now only way. With a single Azure Key Vault and Microsoft Entra ID app, you can switch RSAT to the new model without breaking a single test case.
What’s changing—and why it matters:
- Existing RSAT certificates will stop working.
- RSAT doesn’t support app-only tokens, so test executions must impersonate actual users.
- Multi-Factor Authentication on test accounts causes silent failures; disable it for RSAT identities.
Prerequisites:
| Item | Detail |
| Test accounts | One per sandbox; MFA disabled, never re-used in PROD |
| Azure Key Vault | One vault per tenant to store passwords |
| Azure Entra ID app | App registration that RSAT will use to read Key Vault secrets |
| RSAT 2.x | Latest build installed locally |
Configure the solution:
1️⃣ Prepare your Key Vault
- Create a vault (or choose an existing one) in the same tenant as F&O.
- Add a secret per test email id user Name pattern: strip symbols from the e-mail →
john_doe@contoso.com→johndoecontosocom.
Value: the exact password.
3.Rotate secrets and account passwords on a schedule (e.g., every 180 days).
2️⃣ Register an Entra ID app
- Go to Azure Portal → Entra ID → App registrations → New app.
- Record the Application (Client) ID.
- Create a Client Secret; copy the Secret ID and Secret Value.
- In the vault, grant the app Get & List permissions for secrets (Access Policies or RBAC).
3️⃣ Point RSAT to the vault
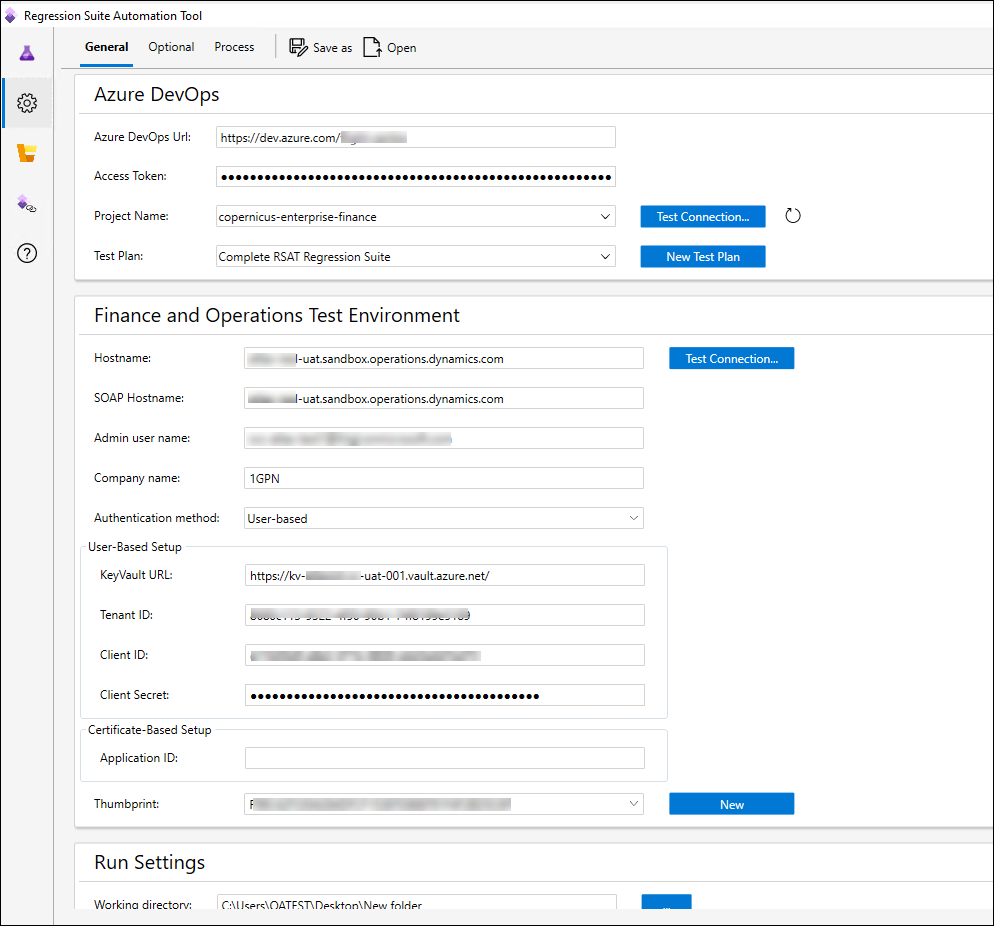
- Open RSAT → Settings → Authentication and choose User-Based.
- Fill in:
- Tenant ID
- Key Vault URL
- Client ID
- Secret ID and Secret Value
- Select or generate a local certificate thumbprint (RSAT uses this only to encrypt its config).
Best practices:
- Sandbox-only identities: never map RSAT to real production users.
- Tight RBAC: give the Entra ID app the minimum required Key Vault rights—nothing more.
- Secret expiry diary: add a calendar reminder a week before the client secret expires; update RSAT the same day you renew it.
- Audit regularly: verify that no test account has drifted into the PROD tenant or regained MFA.
By shifting RSAT to user-based authentication backed by Azure Key Vault, you stay compliant with Microsoft’s certificate retirement and keep test runs fully automated. Set it up once, rotate secrets on schedule, and your regression suites will continue to hum along—no certificates, no MFA roadblocks, just smooth continuous testing.
Reference : User-based authentication
Need help? Connect Atul
- Key Vault parameters in Dynamics 365 F&O - July 29, 2025
- User-based authentication RSAT - July 22, 2025
- Boost First-Load Performance in Dynamics 365 F&O with IIS Preload - July 15, 2025